Welcome back to This Week in Privacy,
our weekly series where we discuss the
latest updates with what we're working on
within the Privacy Guides community and
this week's top stories in the data
privacy and cybersecurity space,
including how lockdown mode thwarted
forensics tools,
Windows reconsidering their AI tools,
and more.
I am Nate,
and joining me this week is Jordan.
How are you doing, Jordan?
I'm good, thanks.
Happy to be here again,
returning on the podcast.
It's good to be back.
Yeah, it's been a minute.
Glad to have you back.
It's exciting.
Yes, a very exciting week this week.
Indeed.
Real quick, for those who don't know,
Privacy Guides is a nonprofit which
researches and shares privacy-related
information and facilitates a community on
our forum and matrix where people can ask
questions and get advice about staying
private online and preserving their
digital rights.
This week,
we are jumping straight into the news and
we're jumping straight in with a story
about how the FBI could not get into
a Washington Post reporter's phone because
of lockdown mode.
Um, so this story is admittedly not super,
super detailed.
Um, I mean,
I guess it's about as detailed as one
would expect, but, uh, let's see, where's,
oh, my screen popped off the stage.
Sorry about that.
Y'all let me go ahead and add that
back real quick.
Uh, shoot.
Hold on.
I think I'm hitting the wrong button
twice.
Yeah.
Okay.
There we go.
Got it.
Okay.
So this story comes from four Oh four
media.
Let me scroll up to the top here.
And, um,
You know, the title, like I said,
the title really says it all.
So the FBI did have a warrant.
That's a nice change of pace here.
The FBI had a warrant and they went
to a Washington Post reporter's home and
seized a bunch of devices.
And specifically,
they say that when they plugged in the
iPhone to their forensics tool to try and
extract information, they couldn't.
There's some interesting stuff here that
we talked about behind the scenes this
week and we were trying to figure out.
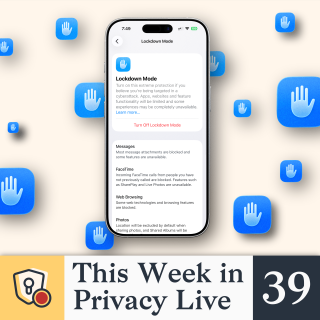
They said there was a notification on the
device's home screen that specifically
said it's in lockdown mode.
And those of us here at Privacy Guides
that have iPhones,
we were kind of playing around with it
and turning on lockdown mode and plugging
it in and trying to like,
can we recreate this?
Because I've never heard of that.
And as far as I know,
none of us were able to recreate that.
So we think this may have been a...
This may be or I think this may
be like something specific to that tool.
Like maybe when you plug this thing into
the forensics tool, it pops up and like,
oh, lockdown mode is enabled or something.
But yeah.
And then here's like a little screenshot
for video viewers.
Here's a little screenshot of the warrant
that or the court record that says that
they were unable to get it.
So.
I guess just to kind of round out
this story,
there is kind of some bad news,
which is that they were still able to
get the information because they had the
reporter access her MacBook.
And specifically...
This is interesting.
They told her to use Touch ID.
They asked her for a Touch ID or
a password, which, for the record,
I have it on good authority from a
lawyer.
You don't ever have to hand over your
password.
That is a violation of, I believe,
the First and Fifth Amendment here in the
U.S.,
But Touch ID, they can do.
They can make you unlock the device or
enter biometrics.
You just never have to specifically hand
over your password.
She said that she does not use biometrics,
but investigators told her to try anyways.
And they say when she applied her index
finger to the fingerprint reader,
the laptop unlocked.
And then they were able to, excuse me,
it says they have not yet obtained a
full image.
But they did take photos and audio
recordings of conversations stored in
Signal.
So a lot of lessons to learn here.
And I do wonder,
not to be a judge or anything,
but that's really not going to go over
well that she's like, oh,
I don't use biometrics.
They're like, we'll do it anyways.
And then it worked.
So, you know,
is that going to be like,
who's that New York mayor that was like,
oh, I lost my phone.
And it's like, yeah, sure you did, buddy.
Anyways.
So this is a man.
There's so many things to take away from
this story.
First of all, I guess to address the
I don't want to say elephant in the
room, but to address the headline,
these stories are useful because iPhone is
closed source, right?
And I think it's really cool to get
this kind of insight and confirmation that
things like lockdown mode do work and they
do provide that benefit that we're
trusting them to provide.
And
I know that in a perfect world we
would use something open source,
but I don't know.
The point I'm getting at is regardless,
it's still good to know that these things
work,
and it's good to have this kind of
third-party confirmation,
even if it's kind of unfortunate that it
has to come that way.
And the other thing that really jumped out
at me is,
like I said at the end there,
they were still able to access Signal
because her device was unlocked.
And I think that's a really important
thing to talk about because a lot of
the time we see this –
abused in the news or twisted in the
news where they're like, oh, my God,
they access this person's signal.
And it's like, well, yeah,
if the device is unlocked,
of course they did.
So these tools,
all tools have limitations, right?
There is no perfect tool out there.
But it's important that we take it.
First of all,
it's important that we know that.
So if you send anything, you know,
I've said in the past on other recordings
that anything you put in a digital format,
you should be prepared for the possibility
that
It may end up in a data breach
or something like that.
So keep that in mind.
But also,
it's important to enable things like
disappearing messages to keep in mind that
there's only so much we can do from
the endpoint itself.
So I think those were kind of my
takeaways from this story.
Jordan,
did you have an opportunity to read this
story?
And did you have any thoughts on it?
Yes, definitely.
Uh, it's good coverage there from, uh,
from you just there.
But I think that, uh,
one thing that was quite interesting about
this story is, um, the, uh,
four or four media article kind of goes
into, uh, some,
some more detail about the reason why,
like,
I think we should talk a little bit
about why lockdown mode is kind of able
to thought these sort of, uh,
police forensic tools, um,
And one of the most important things that
the lockdown mode actually does is it
disables the device connections.
So if you connect your iPhone or iPad
to a computer,
the device needs to be unlocked.
So without lockdown mode enabled,
sometimes it can actually automatically
connect to a computer without explicit
approval.
So...
that can allow mobile forensic tools like
GreyKey and Cellebrite,
which is like the common police forensic
tools to basically be able to extract
information from the device.
And we've seen this as well with Graphene
OS,
they have a similar setting in the
settings where you can control the USB
connection and allow, you know,
change the options that are required if
you connect the device to another
computer, right?
And as you can see on the screen,
Nate's brought this up here.
It's the Apple support page about like the
specifics of lockdown mode.
And another thing that these forensic
tools do is they often utilize
vulnerabilities in, you know,
software and hardware and with lockdown
mode enabled it kind of protects you in
on both fronts right because it stops the
device connections which can sometimes be
uh exploited with vulnerabilities and also
it disables a lot of these you know
quality of life features but ones that are
often used in exploits and vulnerabilities
such as like you know complex web browsing
uh
um like tools are disabled in this case
it says certain complex web technologies
are blocked which might cause some
websites to load more slowly or operate uh
correctly so you know as well as you
know some it disables some of the apple
services as well so i think this is
quite an interesting story to see that uh
lockdown mode actually did provide quite a
benefit to someone,
especially in like quite a vulnerable
position.
It's good to always see that this tool
that Apple has put out is actually helping
journalists in the field.
But it is another thing that's kind of
a bit of an unfortunate thing with this
case that
Nate kind of talked about was that they
were kind of able to bypass the entire
process because she had her MacBook with a
Touch ID.
And I think it'd be really good if
you could, Nate,
if you could elaborate a little bit.
You said there was laws around the First
and Fifth Amendment.
Could you maybe go into what exactly that
means and why Touch ID can kind of
bypass that?
Yeah.
Yeah.
Real quick.
Thank you for mentioning graphene because
officially privacy guides are our top
recommendation for a phone will always be
a graphene phone because it really does
have the best privacy, the best security.
But there's lots of reasons people may
want to use an iPhone.
Like there are some countries where pixels
are not available and things like that.
But yeah,
graphene has some very granular controls
over the USB port.
uh, port, but yeah, the,
so the first and fifth amendment here in
the U S, um, the first,
the first ten, I believe it is.
It's been a while since I was in
school.
Um,
the first ten amendments in the U S
constitution are called the bill of
rights.
And they were,
I think the first ten that like existed
when the country,
when the U S was founded.
And, uh,
The first specifically is – I mean a
lot of them have multiple parts,
but the first mostly pertains to freedom
of speech.
The government is not allowed to infringe
on your freedom of speech or your freedom
of expression,
your freedom to lobby the government for
complaints, things like that.
And then the Fifth Amendment is the one
that protects against self-incrimination.
So for example,
if any of you have ever watched a
cop show that's set here in the US,
which I'm sure is most of them,
the Fifth Amendment is the one that when
people say, I plead the Fifth,
I'm not going to talk.
What's the word?
I invoke my right against
self-incrimination, whatever.
There's a million ways to put it.
But
basically the reason that this passwords
and stuff like that fall under this is
because first of all,
they can't force you to give up your
password because that one,
and that's the one I'm not sure of,
but I feel like I read this somewhere
that would fall under free speech.
Like they're kind of forcing you what to
say,
but it definitely falls under the fifth
amendment because you have a right,
whether you're guilty or innocent,
you have a right to not give,
incriminate yourself um that's kind of the
way the u.s justice system the u.s justice
system is supposed to work is it's
supposed to be that and i don't want
to get too far off topic but on
paper the way it's supposed to work is
that the defense is supposed to prove that
you are not guilty no matter what and
the prosecution is supposed to find the
truth whether that's you're guilty or
you're not um which is a subtle but
distinct thing anyways so yeah there's
this protection against
Admitting and confessing if you don't want
to.
I mean, obviously, if you want to confess,
you can confess.
Nobody's going to stop you.
But yeah,
so it falls under that because giving up
your passwords could incriminate you.
And therefore,
you are not required to do it.
But like you said, there's workarounds.
Biometrics...
I want to say is a gray area.
I could be wrong about that because, well,
real quick,
let me say I know for sure that
you can be ordered to unlock a device,
whether that's putting in the password and
then handing it over,
scanning your fingerprint, whatever.
That is something the court can force you
to do.
Biometrics,
I've heard conflicting reports,
and a lot of these – we talked
about this last year with the person who
was charged for wiping their phone,
which was also a four-oh-four story.
Phones and biometrics and things are
really in a gray area right now legally
in the US because some courts have ruled
that you need a warrant to search phones,
and other courts have ruled, no,
you don't.
And they're kind of at odds,
and we're kind of waiting for the Supreme
Court to weigh in and settle the matter
once and for all.
And yeah,
biometrics kind of fall under that
category of even if you do need a
warrant or whatever,
it would still be something that they can
force you to unlock the device because it
doesn't really fall under those those same
purviews of like against
self-incrimination and stuff.
It's.
Yeah,
it's a fun gray area right now in
the US.
Right, yeah.
It is kind of, it's definitely tricky,
especially for me as someone who's outside
the US seeing what's going on.
It is kind of hard to follow some
discussions around it.
So it's good that you kind of explained
the situation.
But I think another important thing about
this story that you kind of touched on
a little bit when you were doing the
initial coverage here was that when they
were able to unlock the device,
the MacBook in this case,
there was actually a signal application on
the MacBook and they were able to take
evidence from that signal application on
that MacBook.
And I think that's like a really important
thing that we need to discuss because I
think people need to be careful about
using Signal desktop applications because
of this instance, right?
Desktop computers have less security
protections than a mobile device.
And in this case, it's...
less of a security issue,
more of just like an unfortunate
circumstance where someone had biometrics
enabled, but it does kind of show that,
you know,
your security is only as secure as your
weakest link, right?
As soon as you have one link that
breaks your entire signal history is going
to be available to whoever's trying to
attack the device.
So I thought that was quite an interesting
part of the story actually.
Yeah, definitely.
It's... Yeah, and it's...
You're definitely a hundred percent right.
Like I heard...
I forget who it was,
but somebody on Firewall's Don't Stop
Dragons was talking about...
Phones are almost like,
from a security perspective,
it's almost like we took all the lessons
that we learned from computers and
integrated them into smartphones.
So smartphones are, for example,
smartphones rarely have their updates mess
up.
I'm going to take a fun little pot
shot at Windows here.
When I bought my first Windows eight
computer...
brand new fresh out of the box i
opened it i booted it up and it
failed to install and had to reboot and
it got it on the second try but
uh i've never seen anything like that
happen with a phone right like phones
almost never don't update and they have
significantly better security all around
um you know they they have better
sandboxing and all kinds of stuff i'm not
really an expert on phones but i know
they're significantly more secure but even
so yeah i think i think the
I think it just kind of goes back
to not just the security,
because there's so many aspects of it.
That certainly is a good point,
that desktop devices are generally less
secure,
but also just being mindful of
you know, backups, right?
Like backups are a good thing to have,
especially in the privacy community.
We're really big fans of not using the
cloud, generally speaking.
And it's like, okay, that's great.
But what happens if, you know,
there's a house fire or you're, you know,
there's a flood or anything.
What happens if you get robbed?
You know,
especially like I need to buy a new
one.
I used to have a little external portable
hard drive that was my backup drive.
And the first thing I did was encrypt
it because I knew I'm like,
if somebody breaks in,
they can grab that right off the desk
and go.
Like there's no friction to stealing that
at all.
So yeah, just keeping in mind every,
again, all the end points.
And we talk about that,
I think in the privacy community,
we think about that a lot in terms
of,
the far end,
like I see a lot of people who
criticize encrypted email because they're
like, oh,
most people don't use encrypted email.
So, you know,
it might be encrypted while it's in your
inbox,
but it's still unencrypted in their inbox.
And which is a valid but different
argument.
But the point is, like,
we don't always think about it in the
context of, OK,
but now there's a second copy of your
data on your end of things sitting on
that external hard drive on the desk or
sitting on that computer desk.
you know,
synced up through Signal or whatever
that's less secure.
Or, you know,
some people run a NAS and they use,
what is it,
like SyncThing to sync their data.
And it's like, okay,
now you've got this constantly running,
twenty-four-seven device sitting in the
corner that's syncing all your calendar,
your contacts, your data.
So, yeah, it's really important to,
when you do that threat modeling and you
start building your
your security posture,
I guess we'll call it.
It's important to have that moment where
you stop and think about every step of
the chain.
You know,
what happens if this gets compromised?
If this threat happens, break-in, flood,
you know, it's, yeah.
I mean,
it's really important to think about that
whole picture and not just think like,
okay, I'm using Signal, I'm good.
Yeah, definitely.
Your security needs to be like...
very,
your plan needs to be very clear and
multi-layered.
But I think another thing that's also kind
of important in this story is the person
that had the iPhone seized,
it was actually only an iPhone XIII,
which isn't, you know,
one of the latest generations of iPhones
that has more of those hardware security
features like the iPhone XII,
which has
mte memory tagging enforcement so it's
interesting that even an iphone with
lockdown mode enabled was able to block
these sort of forensic tools um which i
think kind of shows the power of this
of lockdown mode itself actually um
because you would expect an older device
is probably more likely to be exploited
because of its age, right?
Through hardware vulnerabilities and stuff
like that.
And because it doesn't have that updated
hardware, it's kind of surprising.
So that was another thing that was quite
surprising to me in this story.
Yeah, I think I missed that part.
Thank you for bringing that up.
I did see people mention that.
Now that you mentioned it,
I saw people talking about an iPhone XIII
with lockdown mode, but for some reason,
my brain didn't make the connection.
Obviously,
we're always going to encourage people to
do the best they can and use the
latest devices and the best security
measures,
but I think that also I would like
to use that as an opportunity to remind
people that
there's a lot of factors that go into
security.
Cause I know there's some people that
maybe can't afford like a brand new device
or, uh, you know,
for a lot of reasons,
like environmentalism,
like I don't want to throw out this
perfectly good iPhone.
Um,
I don't know if the iPhone is still
getting updates, but I assume so if,
if lockdown would work, but, uh, you know,
my point being like,
I'm one of those people,
like I have a pixel six a,
and I plan on using it probably until
next year when it stops getting updates.
And you know, it's,
when that happens,
I want to get the latest pixel so
I can get all these nice hardware
features.
But I think that's just what I'm getting
at is that's,
that's part of threat modeling as well is
like, will this meet my needs?
Will it is, is this,
am I doing enough to protect myself?
And I think sometimes we can feel like
we always have to do more because privacy,
there's always more to do in privacy.
There's, there's always new, new tools,
new ways to improve your privacy and,
unfortunately, new threats popping up.
But you know, that's,
that's one of the reasons that we do
threat modeling is to try and make sure
that we are hitting those goals,
we are doing what we need to to
protect our data.
And
Yeah,
I guess what I'm getting at is as
long as you're fulfilling your threat
model,
it's okay to give yourself some grace if
you're not going as hardcore as you would
like to.
Keep going, keep trying to get there,
but as long as you are meeting your
threat model.
And that doesn't necessarily mean you have
to run out and buy the latest thing
because now it's got this new hardware
feature, but try to if you can.
Again, I want to reiterate that,
but this is why threat modeling works.
Exactly, yeah.
And on the topic of protecting your data,
let's head into this new story here.
And this is Notepad++ update feature
hijacked by Chinese state hackers for
months.
So Chinese state-sponsored threat actors
were likely behind the hijacking of
Notepad++ update traffic last year that
lasted for almost half a year.
The developer states in an official
announcement today.
So that's quoting from the bleeping
computer article here.
A statement from the hosting provider for
the update feature explains that the logs
indicate that the hacker compromised the
server with Notepad++ update application.
External security experts helping with the
investigation found that the attack
started in June of twenty twenty five.
So I guess for anyone who's not on
the
who doesn't use Windows,
Notepad++ is basically an advanced version
of Notepad that has a lot of the
features that you would expect in,
you know,
advanced note-taking applications like
syntax highlighting and such,
so it definitely builds upon the Notepad
like piece of software that's available in
windows.
It's basically like a fully featured
alternative to that.
And it's actually extremely popular.
So that's why it's extremely concerning
that the update feature has been hijacked
by Chinese state hackers.
And just quoting from the article again
here,
the attackers specifically targeted
notepad++ domains with the goal of
exploiting insufficient update
verification controls that existed in
older versions of notepad++.
So basically in December,
Notepad++ released version eight point
eight point nine,
which addressed a security weakness in its
Win GUP update tool after multiple
researchers reported the updater would
receive malicious packages instead of
legitimate ones.
And there was a great post on Mastodon
that I saw by security researcher Kevin
Beaumont,
where he warned that at least three
organizations were affected by these
update hijacks.
which were followed by hands-on
reconnaissance activity on the network.
So yeah,
this is kind of a pretty concerning story,
especially because it's such a popular
piece of software.
Like a lot of people on windows that
are editing text files will be using this
software.
So it is kind of concerning,
but just handing it off to you here,
Nate, what are your thoughts so far?
Yeah, I will admit,
I use Notepad++ on Windows.
So that was a fun headline to read.
I think I say this partially to make
myself feel better.
One thing to note in the article is
it does mention that this attack was very
targeted in that the attackers very likely
only targeted specific users of Notepad++.
so probably hopefully not me but they
could have just as easily targeted me
right um and actually real quick on that
note i think here at the bottom of
this article yeah um there's some links
they talk about this group called rapid
seven that did research on this and they
released an analysis a technical analysis
of the malware and they do include um
how to check and see if you were
compromised i i believe they concluded a
What is it?
Caches of specific files, basically,
that you can check and see if you
have the right file or a compromised file.
So if you are worried that you may
be impacted by this, first of all,
go ahead and update to the latest one
because hopefully that should fix it and
close off access.
But also you can double check that to
see.
But yeah, it's really not a good feeling.
And it's really unfortunate because...
Notepad++ kind of checks all the boxes
that we would normally advertise for a
good privacy tool, right?
I mean, it's open source.
As far as I know, it's offline.
I'm sure it pings for updates and stuff,
but it's not a cloud-based notepad.
It's...
It's very actively maintained.
The developer is very active.
But it just... This happened.
And it's really frustrating because I was
sitting here when I was reading this story
and I was taking notes for the show.
I was thinking to myself,
what's the lesson here?
Because normally the lesson is try to
stick to open source or try to make
sure you only get it from official
sources.
But when there's a supply chain attack
like this, they're really...
of just not what you can do i
guess so yeah i don't know this this
is a really unfortunate story i think my
takeaway is and i know i already said
this in the last story but just to
to remember that um
I mean,
nothing is unhackable and it's important
to be aware that anything you put in
a digital format.
And this is actually one of the things
I like about notepad is you don't even
have to save it.
Like I have literally like seven open
notes that I haven't saved for weeks and
I should really do something with them.
But you know,
that's one of the things is it'll like
hold onto those notes, um,
without having to save them.
And so even if you don't save it,
if it's any,
any kind of a digital format, it's,
it's at risk.
And I hate to say that cause that
feels like paranoia, but, um,
Yeah, that's kind of, I don't know,
is there any better lesson that you took
away from this one or?
Yeah,
I think this is kind of an unfortunate
circumstance, right?
But I think it does need to be
said that, you know,
open source tools are just as vulnerable
to being exploited by these sort of things
as closed source ones.
You know,
just because a tool is open source doesn't
technically mean that this wouldn't have
happened or this would have happened,
right?
So I think that's one thing to consider,
but I think when it comes to note
taking tools and such,
I think it's important to use tools that
have been independently verified, right?
So if a security researcher had done an
audit on this piece of software,
for example,
I think it would have been pretty obvious
that this was a mistake in the update
process, right?
Any security researcher that would have
had an eye over this,
would have noticed this.
So, you know, I think it's
unfortunate,
but I think there's things you can do
to make sure that the software you're
using isn't, uh,
doesn't contain easily exploitable stuff
like this.
So, you know, with privacy guides, we,
a lot of times we require independent
verification by security researchers, um,
or like a security firm,
such as like cure or other ones.
Um, so that is,
that is something you can do to try
and mitigate some of these concerns.
But in that case as well, it is,
you know,
Things get missed.
Not every single piece of software is
infallible.
And I think, yeah,
someone in the chat said,
JS said a secure OS could help a
lot.
Yeah, exactly.
So if you have an operating system that
has more control over the sandboxing of
applications, for example,
I'm sure Nate would like to talk about
cubes,
but there's all sorts of things you can
do on Mac OS and Windows even has
some sandboxing capabilities.
So I think that is another important thing
that people need to think about, right?
Having adequate security protections and
sandboxing and separating tasks into
separate areas can definitely reduce the
damage of an attack because in all
circumstances, it's possible.
Every piece of software can be exploited.
So trying to reduce the damage that can
happen is definitely a good step in the
right direction.
Yeah, I'm glad you mentioned audits,
because that did completely slip my mind,
because audits are really good.
And I do want to point out that
audits, and you did kind of mention this,
things can still slip through the cracks,
because audits are a snapshot of code at
a specific point in time.
So it's entirely possible that Notepad++
could have been audited in June,
or let's say May,
And then this happened like the following
month and there's really nothing to
protect against that.
But another thing,
another advantage of audits is that they
tend to show that an organization is
really serious about their security and
securing their supply chain and stuff like
that.
And, um,
Again,
I want to point out like audits are
also really expensive.
So just because a company doesn't get an
audit doesn't mean that they're not safe
or they're not taking it seriously,
especially if it's like a really hobbyist
project.
Like I think notepad plus plus,
if I remember correctly is donation only.
So they probably don't have thousands of
dollars to invite cure fifty three to come
in and look at their code.
But for those organizations that do have
that kind of money, like Proton, Moldad,
IVPN, I know there's plenty of others,
but
signal.
When they bring in auditors and have them
look at their code and they have that
kind of resource, it shows that, again,
like you said,
things can slip through the cracks,
but it's a really good sign because it
means that they probably have a culture of
security and it's less likely for bad
things to happen.
So yeah, I'm glad you brought that up.
Um, and yeah, I mean, if you want,
I will say cubes or, you know, there's,
there's plenty of other ways to do this,
but, uh, yeah, I,
I am using cubes right now in front
of me for those who didn't know.
And, um,
that is one of the things I like
about it is the compartmentalization of,
I literally have a cube for privacy
guides.
I have a cube for my personal stuff.
I have a cube for banking.
And, uh, if,
if one of my software was to become
in, um,
I don't know why my brain refused to
pick a word there.
If one software I use became compromised
and impacted,
it would limit the damage to that specific
cube, which is still suck,
but at least it would limit the damage,
right?
So yeah,
compartmentalization and secure OSs and
things like that really do go a long
way.
All righty.
Before we move on to the next story,
we're going to pause here briefly to give
an update of what's been going on behind
the scenes at Privacy Guides.
Um, so yeah,
we're going to talk about Ram shortages
affecting the raspberry PI,
but first in case you guys didn't hear
our smartphone security course is now open
to the public or the first part of
it is.
So there's a,
there's three parts technically kind of
four,
cause we have like a little intro video.
And then from there,
it branches off into Android and iPhone,
and there's a beginner and intermediate
and an advanced level.
The beginner level is now open to the
public.
I will let Jordan talk about the
intermediate iOS video in a second.
But yeah, the beginner video focuses,
if you guys haven't seen it yet,
I do think it's on PureTube now.
I could be wrong about that,
but I'm pretty sure it is.
The beginner video focuses on things that
are really subtractive instead of additive
to make your phone more secure.
So things like removing apps you don't
use,
changing the settings and things like
that.
which I think should be doable for a
lot of people because even simple things
like downloading Signal or switching to
Brave or Firefox,
those are things that require people to
take action, right?
They require them to go download an app,
sign up for an account,
no matter how easy.
And I think some people...
I think it's a mental block that some
people have a hard time doing that.
And so the beginner level is things that
anybody can do anytime, right?
Like you're laying on the couch,
instead of doom scrolling,
start deleting apps and stuff like that.
So yeah,
I'm really excited that that's out to the
public now.
And I will turn it over to Jordan
real quick to give us some updates on
any upcoming videos if you'd like to,
or if you want to hold off on
that.
Yeah, thanks.
So I guess, yeah, like Nate said,
we've got the intermediate smartphone
security guides coming out soon,
and we've already got the Android version
done,
and the iOS one is pretty close as
well.
So I'm hoping possibly early next week we
can get that published for members.
And if you're a member,
you can get early access to videos,
just a reminder.
And that was sort of covering,
I guess I should say,
this whole smartphone security course has
been written by Nate and overall direction
by Nate here,
which I think he did a great job
with.
And I think it'll be really,
really useful to people.
We've already had the beginner ones
released to the public,
and we already had some really good
feedback on those videos.
And that's just the beginning.
So the intermediate ones dive more into
things that, you know,
are less to do with your device and
more to do with the services that you
use and the applications that you're
utilizing.
So for instance, you know,
moving to encrypted email providers
instead of using a plain text one like
Gmail.
I'm not going to give too much away
just because I don't want to spoil the
video.
But we also do go into some of
the things on Android,
such as alternative app stores.
So if you're interested in that sort of
thing,
you're not all the way into the advanced
area,
definitely look out for those videos next
week.
And we should have the advanced
series coming out shortly after that as
well because that's you know quite a bit
shorter than the intermediate ones and
Nate's kind of been on fire here he's
been like writing so many videos up and
sending the footage over to me so we've
also got another video in the works which
is the private messaging video which we're
working on there's also I guess we haven't
released have we released this yet
We're also working on a video about
private browsing.
I'm not sure if that's actually released
yet.
Is it, Nate?
That's a good question.
The wheels are turning.
I know because you've sent me the preview
versions,
but I don't know if we've published those
to members yet.
We're going to have to follow up on
that one.
I don't think we have.
All right, then.
I guess members, be ready for that.
That'll be coming out hopefully after the
stream if we can line everything up.
But that's also done.
So that was another video that Nate's
scripted and put together the footage and
recorded.
And that was another really interesting
video, I think,
which is going to be useful for people
to send to people that are stuck using
Chrome or that have misconceptions about
the private mode on Chrome because
it's called incognito mode,
but you're not really very incognito.
So I think that'll be an interesting video
for some people to send to their
relatives, family, friends, you know,
get people moving off Chrome.
I think it's one of the easiest things
you can get people to switch, you know,
instead of Chrome, use Firefox, you know,
instead of
using incognito mode,
you could use more bad browser instead.
And that's really a private way to browse
the internet.
So that's kind of what it's looking like.
We've got that look out for the private
messaging video.
That's what we'll be working on next week.
And yeah,
I guess I can throw it back to
you, Nate.
Is there any other things that we've been
working on this week?
I know we've got a few more news
articles coming out this weekend.
I, I tried really hard to,
Throughout the week,
I will collect news stories that I'm like,
oh,
this is important enough that I think we
should write a brief about it,
but it's not necessarily important enough
to put in the podcast.
And I keep telling myself every day,
I'm like, all right, just take, you know,
ten minutes, twenty minutes,
write up a little quick,
short thing about this.
And then for some reason,
by the time I get done with my
work for the day, I'm so tired.
So my point being, I end up, like,
stacking them all towards the end of the
week, and I really shouldn't do that.
But...
Yeah,
we do have a bunch of those coming
out, maybe half a dozen or so.
And some of those are from me,
some are from Freya,
who's one of our regular writers.
So I think that's about it.
Yeah, and just to real quick,
just to kind of address it,
some of these videos we're putting out
right now, I think are very entry level.
And I think they're really good for
sharing with your friends and family who
maybe are not as excited about privacy as
you are, or maybe...
I don't know.
I think most of you guys probably do
a really good job of like sharing the
stuff with your friends and family,
but I guess it's just something you can
share with people.
But the point I'm getting at is don't
worry.
We will still be doing plenty of like
really advanced, uh,
stuff in the future for, you know,
whatever your tech level is.
So if, if you're thinking like, man,
these are really entry level stuff,
it's honestly,
cause we kind of looked at our,
our library of content and went, Oh,
we haven't covered a lot of the really
basic stuff.
So that's kind of what we're doing.
And, um,
we're definitely going to get back into
other stuff as we go.
I think, um,
probably sooner than later here, actually,
probably after this next video,
I would imagine we'll maybe looking to do
in something a little bit more high level.
So
Yeah,
I think one other thing that I guess
we can touch on now,
which should be coming out at least I
would say in the next month or so,
we're working on another section of the
website.
So if anyone's...
I think people should kind of get hyped
for that.
There's been a lot of work behind the
scenes from Em who's been working a lot
on a separate section.
I don't think I'll go into too much
detail about it here because...
There's, you know,
it's still all being finalized,
but it's definitely being worked on.
And I think this is going to be
kind of a pretty big year for privacy
guides because we're expanding in so many
exciting ways.
So I'm really excited to see how that
pans out.
Yeah, definitely.
Em has been super,
super busy working on that.
And I...
I've seen the outlines of how that is
going to be structured,
but I haven't seen the...
What I'm trying to get at is I'm
excited to see it.
I think it's going to be awesome.
I know she's been working really hard on
it, and yeah, it's going to be great.
One more thing real quick before we jump
into the next story is JS left another
comment here about private browsing.
Said Brave has a pretty good strategy with
having ad block included.
Yeah, it's really...
Jonah and I touched on this in last
week's episode, but...
I think in my experience,
one of the best ways to try and
nudge people towards privacy tools is
rather than focusing on the privacy and
the security benefit,
treat that as like a bonus and focus
on how it makes their life easier.
Like I've had really good success with
getting people to try password managers
because I happen to be in the room
when they're trying to log into something
and they're like, oh my God,
what was my password for this website
again?
And I'm just like,
hey,
you want to know how to never forget
your password again?
And I run into those people six months
later and they're like, oh my God,
this is amazing.
How did I live without this?
So yeah, definitely.
I've gotten people to switch to Brave
doing that exact same thing.
I saw two people in a Discord room
I was in having a conversation where
they're like, oh my God,
the ads on this website are obnoxious.
I'm like, have you tried it in Brave?
And like, oh my God, Brave fixed it.
This is awesome.
So yeah,
that is one thing Brave has going for
it.
But I know there's probably ways to
recreate that in something like Firefox as
well.
So yeah, I just wanted to mention that.
Yeah,
it's kind of surprising to see what people
will put up with on the modern web,
like full-page ads,
auto-playing video ads.
Like, oh my goodness,
it's a wasteland out there.
Dude,
I had to turn it off on YouTube
the other day for something.
I can't remember what it was.
Oh, it was our intro video.
I wanted to make sure that the end
cards were, you know,
click here to go to Android,
click here to go to iOS.
Quick note for other Brave users.
And I wasn't seeing the end cards.
And I'm like,
did we not put end cards on there?
And so I turned off my Brave Shields.
I guess I had some optional thing turned
on that got rid of the end cards.
But while the Brave Shield was off,
there was literally like a one minute
pre-roll ad to start the video.
There was an ad on the side.
There was an ad below that.
There was an ad at the bottom of
the video.
I'm just like, oh my God,
how do people put up with this?
It's so bad.
Oh yeah.
So definitely,
I don't know how people live like that.
Speaking of bad things,
there is being an ongoing RAM crisis.
And I don't know if you've seen that,
but one of our previous team members,
Kevin,
he wrote an article about the whole RAM
crisis that's going on.
And unfortunately,
that has now started to affect Raspberry
Pi.
So Raspberry Pis have received another
price hike in the last two months.
And basically, the more RAM the board has,
the more its price is increasing.
So just quoting from this article here
from Ars Technica,
the ongoing AI-fueled shortages of memory
and storage chips has hit RAM kits and
SSDs for PC builders the fastest and
hardest,
meaning it's likely that for other
products that use these chips,
we'll be seeing price hikes for the entire
rest of the year, if not longer.
And the latest price hike news comes
courtesy of Raspberry Pi CEO
Eben Upton, sorry if I said that wrong,
who announced today that the company would
be raising prices on most of its single
board computers for the second time in two
months.
Prices are going up for all Raspberry Pi
four and Raspberry Pi five boards with two
gigabytes of or more of LPDDR four RAM,
including the compute module four and five
and the Raspberry Pi five hundred computer
inside a keyboard.
And the two gigabyte boards pricing will
go up by ten dollars.
Four gigabyte boards will go up by fifteen
dollars.
Eight gigabyte boards will go up by thirty
and sixteen gigabyte boards will increase
by a whopping sixty dollars.
So I'm kind of happy about this in
a very selfish way.
I actually bought a Raspberry Pi like two
months ago before the price hike.
So I'm kind of happy that I decided
to finally replace mine.
But what do you what do you think
about this?
Yeah,
I happen to have a couple of Raspberry
Pis sitting around at home that I'm
actually not using,
and I'm trying to figure out what to
do with them.
And pardon my technical difficulties while
I try to get my screen share back
up here.
But yeah, it's... I don't know.
It's really a bummer because the whole
selling point of the Raspberry Pi is that
they're so cheap, right?
And personal opinion, I think that's a...
I think that's slightly misleading to say
that they're so cheap because they do...
They're very cheap if you just want the
board.
But if you want the case that goes
over it and stuff like that,
I think it becomes a very different story
at that point.
I think the price does start to go
up significantly.
And maybe it's me because I have cats.
And I'm like,
the cat hair will get everywhere.
It will absolutely get all over the board
and everything.
But either way, they're very inexpensive.
And there's certainly...
In my opinion,
I don't think they make for good full
computers.
It's not like, oh,
I got this thirty dollar computer.
They're still definitely.
They're still definitely.
They're made for very specific tasks,
is what I'm trying to say.
They're really popular,
and this is why we're covering them.
They're really popular in the privacy
community for running like a single and
single member Mastodon instance or like a
simple next cloud instance or DNS,
you know,
to block ads and stuff at home.
Um,
ads and trackers and all kinds of stuff.
And so this to me.
Sorry, I know I'm rambling a little bit,
but this to me touches on a larger
issue that I've been trying to figure out
how to put into words and address for
several years now,
which is the idea of privacy as a
privilege.
Because it is really unfortunate when you
have to pay for privacy.
Like kind of going back to phones, right?
We talk about something like Graphene OS.
And Graphene OS is only available on a
Pixel,
which is a several hundred dollar phone.
which is still cheaper than an iPhone.
But it's not a cheap phone.
And again, certain areas can't get pixels.
And so it's almost like you have to
be privileged enough to have the money and
live in the right area to get a
graphene phone.
And that's really unfortunate.
But at the same time,
things like Raspberry Pis,
things like VPN servers,
those things cost money.
And you can't
You can't pay the rent for your office
by, I don't know, telling the landlord,
how do you signal, right?
That's just not how the world works.
So the point I'm getting at is it's
really unfortunate to see this price go up
on these very reasonably priced tools that
are designed to help,
or maybe they're not designed to,
but they're very good for helping people
reclaim control of their data.
And it's really unfortunate to see that
that barrier to entry go up,
even if it's only a little bit.
But at the same time, it's like,
I don't know, some things just cost money.
And that's an unfortunate reality of
especially this situation right now.
So, yeah.
I think this is just another good reason
to really dislike AI.
This is the reason why all of this
stuff is becoming more expensive.
There's all these AI CEOs, tech companies,
they're buying up all the RAM,
they're buying up all the SSDs for running
AI models because they need all that
memory to train and to run all these
models, right?
It's not...
And I think we've kind of seen this
for a while with Raspberry Pi.
It's kind of been a continuing drama with
Raspberry Pi.
They keep kind of,
I don't know if you've noticed,
but over the last couple of generations of
Raspberry Pi,
it's like they've been pushing the price
up and up and up.
And it's got to a point where,
you know, I was looking at,
like I had an original Raspberry Pi from
like, like a Model B.
And it finally died this year after.
Fourteen years of dedicated service.
So I had to replace it.
Right.
And there was nothing that was really the
same price as what I'd paid for that
original Raspberry Pi.
I think I only paid like twenty five
dollars for that original Raspberry Pi.
So I guess I could have bought like
a Raspberry Pi like mini one.
But, you know, I think it's.
Still,
I think it's a problem with affordability,
right?
And I think Raspberry Pi has kind of
been becoming more and more unaffordable
as time goes on.
And I'm not sure if the pricing is
justifiable, in my opinion.
I think there's plenty of alternative
options to Raspberry Pi.
Unfortunately, it does come with,
you know,
downsides such as software support not
being as good and, you know,
just general community support not being
as good.
But I think, you know,
There's definitely, you know,
bargains to be found like JS in the
chat said, I bought a mini PC,
sixteen gigabytes of RAM and one hundred
Intel CPU for one hundred and sixty USD.
Exactly.
You know, I think that's oh, yeah.
So they increased the price of that
because of the RAM shortage.
I think also another another thing with
with these buying new is kind of not
always the best way to go.
Right.
there's plenty of used options for,
you know,
you don't need a Raspberry Pi to run
a couple of small services.
You could always get like a refurbished
business computer,
like a Dell Optiplex or, you know,
these old retired business computers that
they're selling for like absolutely
nothing.
Like you can basically get them for free.
They may not be as power efficient,
but you're still getting the,
ability to run those low powered services.
So I think there is always an option.
But I do think when it comes to
the thing you said about privacy being a
privilege,
I think it's definitely a matter of
perspective.
I think
people can still do quite a lot for
their privacy.
Like a lot of privacy tools are free,
like ProtonMail, Tudor, that's all free.
Like you don't actually need to pay.
Like you can still get away with having
a free account.
And I think it's important to have these
free options, right?
Where, you know,
freemium model is really good in that
circumstance, right?
Like with Bitwarden,
you can have a syncing vault with security
and it's free for the most part.
You miss out on some small features,
but you're getting a lot of those features
that are the most important for free.
And I think, you know,
it is kind of unfortunate that there's
things like hardware where it's a little
bit more tricky with like, you know,
like Nate said, there's Google pixels.
They cost quite a lot of money depending
on what country you're in.
And they can also kind of, uh,
have you know problems with international
uh shipping you know not every country has
has pixels available um it's not a
globally available uh device but you know
I think a lot of people can also
get a really good level of privacy just
by, you know, deep loading their phone,
switching the usage on their device, or,
you know,
instead maybe going for an iPhone,
which is available in a lot of locations.
So I think people don't have, you know,
zero options.
But I do think if you do want
that highest level of security and
privacy,
you definitely are going to need to shell
out some money for the hardware.
But I think when it comes to software,
we have a lot of good free options.
There's a bunch of examples like the Tor
browser.
You can browse anonymously for free.
It doesn't cost money.
But a lot of that is supported by
Tor network operators who do this for the
love of the game.
They're not...
in this to make money.
They're doing it to promote the free
internet,
to allow people to access information.
So I think we do have a lot
of privacy tools that are accessible to a
lot of people.
But there's also that gap that I think
needs to be filled when it comes to
hardware,
because we don't really have very many
affordable hardware options.
Because Google Pixels,
they're starting at like,
five hundred bucks.
And it's kind of hard to shell out
that much money.
A lot of people don't have that much
expendable income to just drop on a phone.
That's why a lot of people,
they go with carrier plans,
like they pay their phone off every month.
So I think we do need to be
thinking about the accessibility of things
and
It'll be good if there was another phone
option that was similar security to a
Google Pixel that, you know,
would allow people to do the same thing,
but with a much more affordable price.
But right now we don't really seem to
have that.
So, yeah, I don't really have,
I feel like I've been talking about this
for a while,
but do you have anything you want to
add to that, Nate?
No, that's fine.
I mean, I ramble plenty.
No, and yeah,
just to back up what you said,
you're absolutely right.
There is so much in privacy that can
be done for free or cheap,
like Signal and encrypted email.
But it's just, yeah,
it's unfortunate that once you start
getting to those higher,
and those things do so much.
How am I trying to word this?
It's the whole like, what is it?
The Pareto principle, like, that,
you know, I think, like,
switching browsers,
switching communication methods,
blocking ads, all that kind of stuff,
probably gets you, like,
There are a handful of, I would argue,
very reputable free VPNs,
but they're also horribly slow and very
limited on their capabilities.
Like you were saying,
it's unfortunate that once you start
getting to those higher levels of
really...
I guess perfecting for lack of a better
word, like perfecting your privacy.
Cause obviously privacy is a journey.
We'll never really get there.
There's no such thing as perfect privacy,
but once you start really doing those
advanced things,
like you mentioned switching to a graphene
phone,
like there's significant barriers and it's
just, it's very unfortunate I feel like.
But yeah.
I don't know.
Yeah.
I think,
I think you kind of summed up all
my, my thoughts on this one.
It is,
It's unfortunate, and yeah,
it's another reason to be mad at AI,
because yeah, this is... Oh my god, yeah.
I'm so mad.
Everything's so expensive right now,
and...
You know,
you and I were talking before the
recording about maybe, yes,
the rain cloud, perfect.
We were talking before the recording that
maybe I might need to get a new
computer and my wife,
she's been having some issues with her
Pop!
OS laptop, which it's not system.
It's literally like a different ThinkPad
that has Pop!
OS on it.
And thankfully we found some stuff online
that we could install and it helps with
the power management.
And so that can has been kicked down
the road, but yeah,
now is not a good time to need
new computers.
So frustrating.
Yeah.
I'm truly sorry to anyone who needs to
buy an SSD or RAM right now.
I still need to buy a backup drive.
Yeah.
I do wonder if hard drives are affected.
That would be interesting.
I was going to say,
I think hard drives are significantly less
affected, if at all.
So it's probably not that big a deal.
But yeah, that's frustrating.
Okay.
We do have one more story real quick,
and I think I got my screen share
fixed here.
And this is about Microsoft and their use
of AI.
Is it going to work?
Oh, hold on one moment.
Yeah,
so this is actually potentially some good
news,
which is that Microsoft is apparently,
allegedly reconsidering how much AI they
are cramming into Windows.
So for those who are fortunate enough not
to have to deal with Windows Eleven,
Microsoft,
on the topic of AI and raising prices
and everything,
Microsoft is part of the problem because
they have been cramming AI aggressively
into everything you could possibly
imagine.
Like,
I'm going to get really niche with my
references here,
but if you guys have ever seen the
show The IT Crowd, which if you haven't,
you should because it's hilarious,
but
In the first season of The IT Crowd,
and I didn't notice this until I rewatched
it years later,
there's EFF stickers literally everywhere.
And I found out later that's because Cory
Doctorow was one of the advisors on that
show.
And he was, I believe,
a board member at EFF at the time.
So he just stuck stickers everywhere.
And then in season two,
there's significantly less stickers
because I think even the EFF told him
to chill out.
So that's basically what Microsoft has
been doing with AI is anything you can
think of, they're slapping AI on it.
And...
This has not gone over well at all,
at all, at all, at all,
because numerous studies are coming out
showing that most people at best do not
care about AI.
Most people either hate it or they're
completely indifferent.
There are very few people that are excited
about AI.
And Microsoft is finally getting that
memo.
Oh, man.
Where do we even begin?
Apparently,
Copilot is integrated into Notepad for
some reason on the topic of why people
use Notepad++ earlier.
It's in Paint,
which I guess that one I kind of
understand a little bit better for
generative AI, but...
I don't know.
If I want a powerful image editor,
I'll probably go with Photoshop or
something.
I don't know.
I'm getting off topic.
But anyways,
I'm just pointing out how deeply they've
shoved AI into everything.
Most notably,
many of the privacy veterans will remember
Recall,
which is one of the most horrifying
privacy invasions of the last several
years, probably.
I said one of, for the record.
It's definitely not the worst,
but it's up there.
Which,
real quick for those who don't know,
it's literally an AI that takes a shot
of your screen, a screenshot,
every couple of minutes or couple of
seconds.
And the idea is that you're supposed to
be able to type into your computer, like,
oh,
what was that website that had the green
shoes that I was looking at or whatever?
And it would go through and it would
be like, oh,
that was this link on Amazon.
The problem is it was so poorly thought
out that it didn't redact social security
numbers, passwords.
It did redact Netflix though.
So we know where Microsoft's priorities
were.
Anyways, anyways, all this hatred aside,
real quick,
just to round off that saga for anyone
who wasn't there,
there was so much pushback that Microsoft
did actually delay it a whole year to
try and fix it.
And by fix,
I'm going to put that in heavy quotations
because it
They made it less obviously terrible,
but it was still pretty bad.
But anyways, according to...
So this article is pretty light on
details.
I do want to acknowledge that upfront.
But this comes from Windows Central and
they have unnamed sources that work at
Microsoft who basically said Microsoft is
reconsidering a lot of things.
Unfortunately,
I don't think most of it's going away
from the way this article's word.
They said they have paused work on any
additional co-pilot buttons for inbox apps
for now.
I do believe there are a few things
that they're still going to go ahead with,
like semantic search, agentic workspace,
Windows machine learning,
and Windows AI APIs.
Microsoft believes that these
under-the-hood AI efforts are still
important for app developers and users,
even though nobody wants an agentic AI
workstation, but whatever.
There is, I can't find it now,
but I think they did say there are
a few things that they're just dropping
entirely.
Oh, sorry.
Okay, so they didn't, here it is.
They didn't commit to it,
but Notepad and Paint,
the ones I mentioned earlier,
they said that those are under review.
So those might get pulled entirely.
What's very also likely is they said that
the company is basically trying to
rethink things uh what they used a
phrasing about copilot that i thought was
or not copilot recall uh recall in its
current implementation has failed though i
understand the company is exploring ways
to evolve the concept rather than scrap it
entirely possibly dropping the recall name
in the process though this is unconfirmed
uh personal opinion they can evolve it
right into the recycle bin where it
belongs but anyways yeah it's it's
So it's,
it's really unclear what direction this is
going to take,
but it is good that they're finally
listening.
And, uh, this is coming,
the article notes,
this is coming on the heels of Microsoft
admitting that windows is horribly broken
right now.
Uh,
it's been in my headlines in my newsfeed
a lot lately and usually not for good
reasons.
And they did commit to trying to quote
unquote, fix windows this year.
Although again,
they didn't really say what that entails.
This is probably part of that.
Um,
I will say that in my opinion,
I think their AI implementation is so bad
that really anything is fixing it at this
point.
Anything they can do to make it less
terrible,
whether that's making it less obnoxious,
whether that's getting rid of it
completely,
whether that's hopefully making recall
less of a privacy nightmare.
I think the very least they should do
is make it optional.
They're probably not going to do that
because this is Microsoft.
I guess I'll just say that.
I don't really have high hopes that this
is going to be revolutionary,
but I am hoping that they can make
it less terrible.
I really think...
I don't want to say that's the only
direction they can go in because this is
Microsoft.
They can definitely find ways to surprise
us,
but I definitely don't have hopes for them
to actually make this good in any way.
I just hope they'll find a way to
make it
Not so bad.
I think those are kind of my thoughts
on this one.
Do you have anything you want to add
to this, Jordan?
I think you're lucky enough not to be
subjected to the nightmare that is
Windows,
but I don't know if you still have
any thoughts.
Yeah,
I've kind of avoided using Windows almost
completely.
I mean,
Mac OS isn't really that much better,
but Linux is definitely a good place to
be right now.
So I think that's, yeah,
I agree with everything you were saying.
You know,
it is kind of frustrating that like
Microsoft is working on stuff that
seemingly not that many people are
actually interested in.
Like, you know,
adding all these AI recall features and
co-pilot things.
I think, you know...
Microsoft is kind of realizing, yeah,
we're going to have to actually add
features to the operating system that our
users actually want.
You know,
like we don't just have to add silly
like AI integrations.
I really hope that, you know,
this is a sign that the AI bubble
is finally going to, you know,
explode because you know these companies
aren't getting the returns on their
investments they were looking for right
they're probably dumping a huge amount of
money into into developing these features
and kind of going all in on AI
because I know like I've seen the CEO
of Microsoft he was saying you know
they're going all in on agentic operating
systems and utilizing all these new you
know developing all these new AI
integrations and I think
it's finally good to see them realize
that, you know,
the majority of people are not really
interested in this and that they're going
to start scaling it back because yeah,
it's,
I guess we should also talk about this
from a privacy perspective.
You know, I think it goes without saying,
you know,
an agentic operating system and operating
system that is basically sharing a lot of
information about your system with,
you know,
a third party because in a lot of
cases, this processing isn't done locally.
You know,
a lot of the processing that is done
for these agentic systems is actually
being sent to a third party service.
And this is kind of terrible for a
lot of reasons because, you know,
information that you thought was private
and was local on your computer is then
basically being broadcast onto the
internet.
Like I know a really good, uh,
a really good thing to think about this,
right,
is let's say you're talking to someone on
Signal on a Windows computer,
and they've got some agentic operating
system features running at the same time,
that could be recording you,
that could be monitoring your call,
and it could be saving that or sending
it to a third party server,
which is breaking the privacy of Signal.
You're just adding a listener on the other
end.
You're just sending this information to a
third party server.
So I think at least some people that
care about their privacy have been saying
this,
but I think it's good that in general
people aren't that interested in this
because if this was to become more popular
and available on operating systems,
it would kind of be a nightmare.
It would kind of be a privacy nightmare
because then you don't really know what
you're sending to another person is
actually private or if it's being sent to
a third party server.
I'm just happy that Microsoft is realizing
that this is a bad idea.
Maybe it's not for the same reasons that
we care about, which is, you know,
it being a privacy nightmare and
destroying any sense of privacy that
people have.
But it's good either way.
I think we can take this win.
Yeah, for sure.
And that's...
That's something that's in the back of my
head, too, when I talk about, you know,
I said, like,
hopefully this will be optional and it'll
be, like, less terrible.
But even optionally, Microsoft is,
or Windows, I mean,
is such a notoriously leaky operating
system from a privacy perspective.
And I don't...
I think I posted it in a group
chat with my friends.
I don't think I posted it in the
Privacy Guides chat.
But a few weeks ago,
I may have mentioned it on here, actually.
A few weeks ago,
I realized that for some reason,
my Windows computer hadn't updated since
version, like, .
It was whatever version just stopped
getting support in November.
And so I was like, okay.
I need to sit down.
I need to figure this out because I
want to make sure I'm getting those
security updates.
And I had to jump through many,
many hoops.
I had to chase down all kinds of
issues.
Eventually, I did get it to update.
Everything went smooth.
But then because it was an update,
it's introduced all these new features.
And it was basically like a whole new
computer.
So I had to go through and I
had to use...
And for the record,
not all of these are equal.
So this is not like a broad endorsement,
but I have very specific third-party
scripts and tools that I trust to like
de-bloat some of this Microsoft stuff.
And I swear to God,
it was like an hour long process to
go through.
And I only have like three of them
that I use,
but to go through all three of them
and run them to get rid of the
telemetry, get rid of the AI,
get rid of this, get rid of that.
And it was such, and that was,
I'm not even talking about the whole
updating process.
I'm talking about just that part of going
through,
making sure all the settings that I want
turned off are off,
making sure that these scripts run,
checking the scripts and making sure I
know what they do and I'm okay with
it.
And just, it was so obnoxious.
And it's like,
it shouldn't be this ridiculous to use a
computer
without giving up all my privacy,
plus the kitchen sink,
plus the neighbor's kitchen sink,
like it's insane.
And so going back to what you were
saying about AI is that's my concern is
that even if they roll this out in
a form where it's optional,
does that only mean optional to the,
like on the end user facing, like what's,
what's the word I'm looking for?
Like,
where it seems optional.
But in the background,
it's still submitting data.
It's still collecting data.
And I'm sure it's less than if it
was running in agentic mode or if Recall
was taking those screenshots every three
minutes or whatever it is.
But it still just worries me that it's
like, yeah,
but this thing could still be running in
the background,
potentially introducing vulnerabilities,
potentially sending more data than it
should be back to Microsoft.
That's what worries me.
And it's such a shame
as somebody who grew up on windows,
like I'm not a windows fan boy by
any measure, but I mean, let's be real.
Like Macs are really expensive.
And I mean,
I guess now they're about the same because
Mac is the only one that can afford
to eat the price hike on Ram,
but you know,
historically Macs are really expensive and
they work great and they've got great
security,
but you are absolutely unarguably paying
for a brand name.
That is a fact.
And then Linux is free, but
historically doesn't always do the things
I need it to do.
I really do want to test some of
my production stuff and see how well it
works.
But I guess my point being is like,
Windows has always been such a relatively
affordable, customizable system.
And it's really frustrating to just see it
become worse and worse and worse in every
sense of the word,
from the UI to the privacy,
to the bloat, to the just,
it makes me sad.
Like I said,
I was never a Microsoft fan boy,
but it's just, it used to be better.
We used to be a society.
I digress.
I've ranted about that plenty.
If that's all we've got for now,
I think there are a couple of quick
stories that we wanted to highlight.
We're not going to talk about these
extensively because admittedly we had this
conversation earlier in the week.
Jonah and I have been covering all the
age verification stuff for literal weeks
and we have nothing new to add.
It's bad.
We're not in favor of it.
We think that there's
better ways to protect children online.
But we did want to let some of
our listeners know,
specifically in Spain and Greece,
if you are Spanish or I guess it's
Greek, isn't it?
I almost said Grecian for some reason.
But if you are Spanish or Greek,
these are
the latest countries who are now planning
to ban social media for children under
fifteen.
So yeah, like I said,
I don't think we really have anything to
add to that,
but if you do live in any of
those countries,
you should be aware of that.
Do you have anything you want to add
to that, Jordan?
Not particularly.
I mean,
I think both you and Jonah have talked
about this pretty extensively,
so I don't think we need to drag
this out,
but
It's frustrating that the start of this,
you know,
was with Australia's social media ban and
now other countries are following.
I think this is basically what we were
saying from the start, you know,
as soon as you normalize this in one
country,
every other country is going to start
following suit and
yeah,
it's kind of unfortunate that that is
exactly what is happening right now.
We warned you,
like we warned them that this is going
to happen and no one was taking it
seriously, but here we are.
So it is kind of frustrating.
Yeah.
It is kind of frustrating that, you know,
we've, we've been here, we've been, uh,
saying it from the start, but, uh,
now it's actually coming true.
So yeah, I think, you know,
do what you can in these countries,
make your contact, your representatives,
you know,
try and educate people in your life about
why this is bad.
Hopefully there can be some,
positives from this like you know it's it
sounds like these are both announcing a
ban they're not actually implemented yet
so there's still a chance for you to
have your voice heard so definitely try
and at least make some noise about it
because in a lot of cases uh if
a lot of people are against this then
you know it will end up being
uh a lot harder for them to pass
this with you know as many uh restrictions
but i guess the the thing to remember
about this is these are both you know
in spain um
I feel like they might have much stronger
data protection laws than that of like
Australia or the UK.
So it's interesting how they're going to
actually be able to implement this
without, you know,
because they're going to have to require
people to provide their ID or do some
sort of facial scanning.
It'll be interesting to see how they're
going to navigate that,
like regarding the data protection laws.
So that'll be something interesting to
watch, I guess,
but definitely try and make your voice
heard about this issue.
Yeah,
I just want to add the slippery slope
is I kind of hate using the slippery
slope argument because it is not always
applied in good faith and it doesn't
always turn out to be true.
But in the case of tech,
I feel like it is true more often
than it's not.
Actually,
a really good example is facial
recognition.
There have been multiple articles and
stories written about how Facebook
invented their little Ray-Ban facial
recognition glasses years ago.
And even at Facebook, they were just like,
no, this is too much.
This is a line too far.
We're not going to do this.
This is creepy.
Until Clearview AI came along.
And once Clearview AI came along and made
facial recognition totally cool,
now they couldn't wait to jump on the
bandwagon.
So yeah,
I feel like with tech in particular,
the slippery slope is true more often than
it's not, which is so, so frustrating.
Absolutely.
With that, in a moment,
we're actually going to start taking
viewer questions.
So if you have been holding on to
any questions about the stories that we've
talked about,
go ahead and start leaving them on our
forum thread or in the comment section of
the livestream.
But first,
we're going to check in on our community
forum.
There's always a lot of activity,
and this week has been no exception.
But we're going to highlight just a couple
of interesting stories that we wanted to
discuss here.
One of them is DuckDuckGo did a poll
that shows that people are against AI.
I feel like I read this story when
it was first published.
But yeah, I mean,
the author of this post sums it up
pretty well here.
DuckDuckGo made a public poll to see what
people think about AI,
and ninety percent voted against.
And I believe this thread has largely just
been people
discussing their opinions about AI.
And I don't know,
we just got done talking about AI and
the RAM shortage and how that's affecting
everything.
Do you have any thoughts about AI, Jordan,
or do you want me to go first?
I mean, I think we can kind of,
you know,
I think we talked about a little bit
before,
but I think for a lot of people,
these...
you know,
AI companies are kind of having a pretty
negative impact on people,
like just at like a personal level, right?
Like they're building massive data
centers.
They're using a bunch of electricity,
which is driving up electricity prices.
It's driving up RAM prices.
Like this is nothing that's good for the
average person.
And all for, you know,
my cool little chat bot I can talk
to whenever I want.
Like, is that really,
is the benefit really worth the cost?
And I think,
for a lot of times people are saying,
you know, maybe not, you know,
this is not really that useful.
So I don't know,
it could just be a sort of
There could be a bias in the sample
here.
Like, for instance,
this could have been posted.
I did see it being posted on Mastodon,
which means, you know,
it's kind of people on Mastodon don't like
AI.
So that definitely could have skewed the
results a little bit.
But I think it's still an interesting
idea, right,
to see and to have a poll go
out like that.
It would have been interesting to see if,
you know,
where a lot of these votes were coming
from and how this was published,
because I think that could have had a
pretty big impact on the results of this
poll.
But I think, you know,
ninety percent is kind of conclusive,
I guess.
So, yeah,
I'm not really not really that surprised
by ninety percent being against it.
What about you?
Yeah, no,
I think that's a really good point,
the selection bias.
I will say,
ninety percent surprises me a little bit
because I know DuckDuckGo is one of those
companies that has integrated A.I.
a little bit.
I think they even have their own like
A.I.
proxy and.
I think it's.
Yeah, I mean,
I think that's a really interesting point
for sure, but.
I mean, my personal opinions,
I definitely like...
We mentioned this on a previous episode.
I like the point that Em made a
few weeks ago about AI in its current
form cannot be private because it scrapes
up so much user data from people who
probably didn't consent.
And I think... This is one of the...
This is one of the... Sorry,
I'm trying to put my thoughts in order.
This is a thing that I've said before
is...
I think there's certain things about AI
that are technical problems in the sense
that they can be solved.
Can be.
Will they?
I don't know, but they can be.
Things like the energy usage.
I think that in time,
I think AI will become more energy
efficient simply because the financial
incentive is there to make it cost less
money or maybe find more sustainable ways
to power that energy.
Um,
I wish they would open up more solar
farms instead of nuclear plants,
but I don't know.
I digress.
Um, but then I think there's,
there's the much harder problems that I'm
not sure if we'll ever be able to
tackle,
which are things like compensating the
people for the data collected,
the training sets, things of that nature.
And I think those are, yeah,
I think those are the things that are,
like I said,
going to be harder to solve if solvable
at all.
And, um, yeah, I think, um,
Not to be pedantic,
but I know there's also a really good
discussion to be made about the difference
between,
because AI is just such a blanket term
that we're applying to everything
nowadays.
And I think there's useful types of AI,
like machine learning that's being used
for medical research and stuff like that,
versus the generative AI that's drying up
an entire lake just to make everybody on
Facebook look like Studio Ghibli.
And yeah,
I think it's really unfortunate that,
I don't know.
It's just really unfortunate.
And also, as a creative type myself,
I'm really annoyed that AI is taking away
all the fun jobs,
like making music and writing stories and
making videos,
and instead of taking away the crap jobs
that nobody wants to do.
Yeah, it's...
It's really unfortunate.
I think it's one of those things that
could be good, but probably,
it definitely is not right now.
And I don't know if we'll ever address
those difficult questions for sure,
but that's really unfortunate.
Yeah,
I think one thing to think about when
it comes to this AI stuff is
I'm not really sure if it could be
done in an ethical way, right?
Because basically the whole, like,
I don't know if you saw,
there was like an article that I saw
about Sam Altman and he was saying if
there was a stop to the wholesale scraping
of the internet for AI training,
then these AI companies literally wouldn't
be able to exist because the data that's
required to train these models is
basically done by scraping the entire
network
entire internet right um so you know i
don't think that like i think people think
about like their personal privacy like i'm
sure i could use like an ai model
locally on my computer that wouldn't be
sending information to a third-party
company but the model itself was trained
off non-consensual like
scraping of people's information and,
and data.
And when you train that model,
you're basically, you know,
encapsulating an entire, you know,
section of the web into a model.
Right.
And that's kind of the antithesis of
privacy, right?
Because if you, let's say you,
you deleted an article that you wrote
about something that could have been
scraped and put inside this model and,
you know, you're basically, uh,
storing this information forever.
And, you know,
it's also storing and scraping a lot of
personal information as well.
So, you know, it's,
it's kind of problematic.
I think there's not really any good way
to do this.
Like I'm sure maybe this,
there's a possibility that someone's made
an AI model based on only
publicly available and consensual data,
but, um,
I'm sure it's not very good and as
useful as the ones that have scraped the
entire internet.
Right.
Um, so, you know,
I think I'm not even certain that,
you know,
if we were able to use completely
consensual data and also have, you know,
use renewable energy,
I think it's just kind of a waste
of electricity as well.
Like electricity is not infinite.
Like it has an impact on the grid,
um,
just delivering electricity to people is
producing carbon.
So I don't know.
I don't think that it's,
I guess maybe our opinions differ slightly
on this, but I think, yeah,
there's definitely, in my opinion,
not really any ethical way to do it
that respects everybody in the process.
That's just my opinion.
No,
and I kind of agree with you because
that was something that I said when I
first mentioned this is like maybe,
and that's why I say those like less
technical problems I think are harder to
solve because like you were saying,
maybe we could,
like I know Creative Commons is working on
a license that basically says, yes,
I'm okay with AI training on this data.
But what if so few people opt into
that,
that
it can't create a good AI model.
And so there is no ethical way to,
to do that.
And, you know, you mentioned the,
the idea of like,
or maybe I just heard you,
you say this, but like,
we can't even like really remove training
data.
You know, we can't,
like we could remove it from the next
iteration when they run the AI and update
it,
but we can't really reliably say that
like, oh,
I want this data removed from the model.
And because of that,
it kind of doesn't respect like the right
to be forgotten,
which to me is personally is a really
big deal to me because I think one
of the most harmful things about the
permanent digital record that we have
nowadays is that
people have almost lost their ability to
grow.
All the older listeners will be with me
on this one.
I grew up pre-internet,
not super pre-internet.
I think we got internet when I was
in my teens,
but it definitely wasn't like it is now.
Social media was not a thing until I
was in high school.
I think Facebook came out when I was
in college.
So I grew up in a world where
You say dumb things.
You do dumb things.
You get in trouble for that,
but then you grow,
and you learn not to do those dumb
things.
And I don't want to sound too political,
but I feel like we're in a world
now where you say something dumb,
and no matter how long ago it was,
it lives there.
And so somebody will go like,
and I guess I'm kind of sort of
talking about cancel culture,
but I don't mean it in that context.
It's, you know,
you say something and somebody will go dig
up a tweet from twenty, you know,
ten years ago.
And it's like, oh,
here's something really bad you said.
And it's like, OK,
but I don't believe that anymore.
I've grown.
I've changed.
Or, you know, it was a.
stupid edgy joke that didn't land well or
whatever it was.
And it just,
it doesn't give us that freedom to grow
and like move on.
And I feel like that's a concern with
AI,
even though it may not necessarily like
directly trace back to you.
It's just,
I don't like that idea of something that
you don't want out there anymore because
you don't believe that anymore.
And you've moved on.
That's still stuck in the training data.
So I don't know.
That's why I said like, maybe,
maybe those,
those harder issues don't have a solution.
Maybe they don't, I don't know, but yeah.
Yeah,
I think those are the harder issues to
tackle if they can be tackled at all.
All right.
There was another thread that we had
written down to take a look at.
This one, the title says,
Android recommendations should reflect
real life,
not just worst-case threat models.
And this author... This author...
basically how would I summarize this?
Cause this is a, um, very,
not an overly long post,
but it's a very detailed post.
And, uh,
Basically, they're disappointed that,
for example, we only recommend graphene.
We don't really recommend other custom
ROMs.
We don't recommend iPhones or anything.
And he mentions some of the stuff that
we talked about earlier,
like some people don't want to buy a
Pixel because it's from Google.
And they don't want to buy a Google
device,
even if they could buy it secondhand.
Or Pixels aren't sold in their country.
Pixels are out of their price range.
And graphene doesn't offer parental
control options.
I definitely have a lot of thoughts on
this one.
Do you need a minute to formulate some
thoughts or do you want to go first?
No, definitely take it from here.
Okay.
So, yeah, I think,
and I'm going to try to paraphrase
something I saw Jonah say,
and I hope I paraphrase this right.
So I apologize, Jonah,
if I get this wrong.
I think with websites like Privacy Guides,
what we try to do is we're trying
to give people the ideal answer.
And I think,
I will say this is my personal opinion,
but hopefully I'm getting it kind of close
here.
I think there's always going to be
exceptions.
So when we say, you know,
like this person pointed out,
when we say like, yeah, the best,
and I went on a little bit of
a rant about this this morning actually on
the forum,
two things can be real,
even when they're contradictory.
Graphene can be the best option for
privacy and security.
But I think there's also situations where
it's perfectly valid that you can't or
won't do that.
Because again,
not sold in your country out of your
price range.
And I think in those situations,
it's really important to
or maybe not in those situations.
I think,
I think it's just important to realize
that, uh, you know, we, we can't possibly,
especially when we make something that is
being mass broadcast,
like a website or like a, uh,
you know, a podcast like this one,
there's always going to be exceptions.
There's always going to be people who have
perfectly legitimate reasons that they
can't do something.
And I think the reason we suggest these
perfect tools is kind of like the idea
of like,
try to get as close to this as
you can.
Um,
But yeah, I mean,
I think obviously I'm going to defend our
choices.
I think there's a reason for the
suggestions that we make.
But yeah,
I guess what I'm trying to get at
is I understand where this person's coming
from,
that there's always going to be exceptions
to the rule and reasons that somebody
can't do something specific like that.
But I don't think that necessarily makes
the advice we give wrong, personally.
But yeah,
we can't possibly cater to every single
exception, every single threat model.
We're trying to give advice that we're
hoping will work for the vast majority of
people in one way or another.
And if nothing else,
I think hopefully it will kind of give
you a direction to aim towards.
And so when you can see,
especially this is something I really like
about the privacy guides website,
it tells you why we recommend these tools.
So when you can see like, oh,
we recommend pixels because they have very
good hardware security.
You know, they have this, they have that.
And if you say, okay, well,
I can't get a pixel,
but what else can I find that checks
most of these boxes or which of these
boxes can I look at that are important
to me?
And I can go find something that checks
those boxes.
So.
Yeah, I think that's where I land.
This was a very popular post.
It's got a hundred and fifty seven
replies.
Holy cow.
Was there anything you wanted to add to
that?
I think this kind of goes back to
some of the discussion that we had about
like, you know,
you were saying like privacy is a
privilege,
like people who have money can afford
these things.
I think, yeah,
it is kind of interesting and important to
at least discuss.
I think that's like a good purpose of
the forum in this case, right?
Like people can discuss these issues.
less perfect tools in a place where,
you know,
people can be critical and talk about it.
But I think, you know, the
The recommendations on the website are
kind of like, you know,
meant to be like the most ideal ones.
I know I've certainly used the forum like
I've been interested in another tool and
I've been like, huh,
I wonder what the people in the privacy
guides forum said about it because,
you know,
they probably looked into it pretty hard.
You know,
people are scrutinizing things a lot.
So I think just because something isn't
listed on the recommendations doesn't mean
that it's not something you can't use.
For instance,
I use a bunch of stuff that's not
recommended by the website.
Doesn't mean that it's the wrong option.
It just depends on your specific use case,
right?
So yeah,
I agree with what you were saying there.
But yeah,
I think this is definitely an interesting
forum to have a read.
I'm not sure if I agree entirely with
what this person is saying.
I think stuff like headphone jacks and
physical SIM slots and SD card slots are
somewhat novelties.
I find that they're not super important.
I think the most important thing should be
the security of the device if you can.
So even if there was a cheaper device
that
could run something that is more private
than stock Android.
I think that would be better.
But yeah,
it's kind of unfortunate that like
Fairphone has,
has got devices that they sell,
but they're also pretty expensive and
they're only available in Europe.
So it kind of limits the,
the availability of that.
And they don't seem to take security as
seriously as the graphing people.
So, yeah, I don't know.
It's kind of an unfortunate circumstance,
I guess.
I mean, I...
I don't use an Android device daily.
I do have one,
but I just prefer an iPhone just because,
you know, it just works best for me.
It's not recommended on the website,
but it's something you can do instead.
And I don't know,
I think people need to make decisions for
their circumstances and you don't have to
a hundred percent follow everything that
we recommend.
It's kind of up to you to make
up your own mind on things.
yeah for sure yeah i don't think i
have anything to add to that so i
guess we'll hop into answering questions
now um unfortunately it looks like we
didn't get any questions on the forum
thread uh i know we kind of
We've, uh,
some weeks we kind of wait a little
bit longer than,
than others to pick headline stories,
just to see if there's anything
particularly, um,
obvious that jumps out at us as like,
oh,
this should definitely be the headline
story.
Um, and I don't know if, uh,
this week people just didn't have enough
time or, or what, but yeah,
it looks like there's not too much there,
but let's go ahead and address some of
the questions in the chat here.
And let's see.
Excuse me.
I guess I'll take this one.
This person I don't think has a display
name.
That or my computer is not showing it.
But I guess we'll say anonymous.
So this is actually in regard to a
question from last week.
They asked if I had a chance to
review the OPSEC Bible.
So last week,
somebody asked about this website called
the OPSEC Bible.
I took a look at it.
I don't know if Jonah did.
Jonah's really busy.
He may or may not have.
I don't really feel like the website was
for me.
I kind of want to reiterate what I
said when you first asked about this
website,
which is I think it's great that there's
different levels of things that cater to
different people.
Because I think there's some people that
when you go up to them and say,
you have to use Graphene,
you have to use SimpleX,
you have to use Cubes,
they're just going to stop listening.
And that may be unfortunate.
That may not be in their best interest.
That may be a mistake.
But that is what they're going to do,
is they're going to stop listening and
walk away.
And I think that's...
That's kind of where some other projects
come in to try and try to
kind of make it a little bit easier
for people to get started on privacy.
And I think some people, most people,
I hope, but I think some people will,
once they start getting into privacy,
they'll realize like, Oh,
this is actually a lot more achievable
than it sounds.
And I can go, you know,
I talked about threat models earlier.
Like I'm a big fan of going above
and beyond.
If you can, a threat model,
in my opinion is kind of more of
a minimum,
like do this minimum to keep yourself
safe,
but feel free to go past that if
you want to.
And, um,
I think it's great for people who want
to go past that and want to learn
how to do some of the more advanced
stuff and use some of the more secure
options out there for whatever reason.
And so I don't really have an issue
with sites that push the more hardcore
things, but I, I don't know.
I just,
I don't think it was for me.
So thanks for bringing it to our
attention, I guess.
But yeah, that was,
that was my thought on that one.
I don't know.
I think I may have shared that one
in the chat.
Did you check that one out, Jordan,
or no thoughts?
Yeah.
I don't really have any thoughts on it.
I think you covered it pretty well.
I think we need to go super in-depth.
that website but i think it's definitely
good to use multiple sources uh for
finding your information right like if we
recommend something don't just take that
as the truth right you should also
investigate other people who are
recommending different things see what
they say as well um so you know
maybe this website could be useful as
another resource to check what
they say about certain things.
And then you can come up with your
own opinion, I guess.
Um, but you know,
privacy guides has a specific way of doing
things.
We're going to choose specific tools based
on specific criteria.
So it kind of is going to differ
to what other people recommend and that's
fine.
Everyone has their own recommendations and
what they recommend.
So I think it's good.
More diverse, uh, information is better.
For sure.
All right, our next question came from JS,
who asked about DuckDuckGo's AI.
You said,
I hear people complain about DuckDuckAI as
a proxy because it just queries the
respective companies,
which in this context,
I think he means like a chat GPT,
Anthropic, whoever.
And you say,
isn't this the same thing that private
search engines do?
From privacy guides, quote,
DuckDuckGo does not log your searches for
product improvement purposes,
or does log your searches,
but not your IP address or any other
PII.
Yes, this is actually...
I don't know.
Personally,
I use BraveSearch because I feel the same
way.
DuckDuckGo itself is just a proxy.
I think most of these meta search engines
do technically draw from multiple sources,
but they usually primarily heavily draw
from one source.
So DuckDuckGo mostly draws from Bing.
StartPage is mostly Google.
And...
I think there's a couple others that I'm
forgetting.
But there are a handful,
like I think Kaji or Kagi,
however you pronounce it,
I think they mostly have their own index
these days.
Brave mostly has their own index.
And I think Mojik is the other one
that they all kind of have their own
index.
So yeah, personally,
I like to use those or I like
to use Brave just because it has its
own index.
I'm already using the Brave browser.
I think they do a pretty good job.
I feel like I'm also just,
I feel like maybe I just,
maybe it's something about me and knowing
how to use search engines the right way,
quote unquote, the right way.
But because I hear some people will get
off of Google and they'll switch to like
DuckDuckGo or StartPage and they'll be
like, oh,
the results just aren't the same to which
number one, yeah,
Google is personalizing your results
because they're stalking you.
But number two, I mean, I just,
I personally have never had that issue.
And I don't mean to like invalidate people
who do have that issue.
I'm sure that must be really frustrating,
but yeah.
don't know for me it's um brave does
the job really well and that's what i
use but yeah that's um
Real quick,
that is another thing that I think almost
all of these AIs, like Jordan was saying,
they're all,
or going back to what Jordan was saying,
they're all kind of just proxies.
Brave's Leo, Proton's Lumo,
and they're done in such a way that
it's a little bit more private for the
end user,
but at the end of the day,
they're still using ChatGPT or Claude or
whoever else,
and
So they still kind of do suffer from
the same privacy problems of scraping data
that they morally probably shouldn't have.
So yeah,
that's all I got on that one.
I think, yeah, there's definitely,
I think there's some valid issues with
these alternative search engines, right?
Like I think one area that is sometimes
not talked about is a lot of these
alternative search engines,
they aren't going to be as good.
I think your location certainly does
matter, right?
Some people complaining about the search
results might be in different countries.
If I search
something that's super relevant in my
country and it doesn't show up,
that's obviously going to be a problem,
right?
And I think it gets compounded even more,
for instance, in different languages.
So if you were searching in a different
language,
I'm sure that is going to be even
worse.
The results are going to be even worse
in Google.
So it is kind of definitely a bit
of a, I don't know,
your use case might vary situation.
Personally, I found that, you know,
I've tried a lot of these different search
engines and none of them have been
particularly terrible.
But, you know,
I find that DuckDuckGo is generally fine.
But I think, you know,
people need to try and see which one
works the best and which one you're most
comfortable with.
I've tried a lot of them and a
lot of them I just wasn't super happy
with it.
And, you know,
it just depends on your use case of
the search engine.
Like not everyone is going to use the
search engine the same way.
So I don't think it's strange to have
an issue with the search results.
Yeah,
I wonder if his point was just kind
of,
maybe what he was saying is it's just
kind of weird that people complain that
like, oh, this is just a proxy.
And it's like, well, yeah,
but isn't the search engine?
But I don't know.
I think that might be more indicative of
the,
general attitudes that people have toward
AI in general.
Yeah, which I guess at that point,
my question would be,
is DuckDuckGo at least keeping...
in line with their ethos.
I hate to take shots at Mozilla here,
but Mozilla's AI integration is absolutely
abysmal.
I don't feel bad saying that,
but their AI integration,
they straight up tell you,
even in their blog post,
I'll give them credit,
they're very open about this,
but they're basically just like, oh yeah,
we've integrated ChatGPT and you can just
click the little button in the sidebar and
it's super easy.
And by the way, once you use it,
you're totally at OpenAI's mercy as far as
privacy goes.
But it's like, what's even the point?
I can just bookmark chat GPT.
I don't need a little pop-up window to
use that.
Why would I use this at all?
So I do have to wonder if,
and I think it does,
but don't quote me.
I do have to wonder if DuckDuckAI is
like, yes, it's a proxy,
but at least they have legal agreements
with the companies not to train on your
prompts or they proxy it so it doesn't
get your
device fingerprint like i have to wonder
if they've done anything to make it more
privacy respecting in which case i would
argue like yes it is still a proxy
but at least they're in keeping with their
ethos of like trying to make it a
more private experience again for the end
user i really want to stress that but
um but yeah i don't know um i
will say real quick in response to what
you said i think my favorite search engine
in terms of actual effectiveness was uh
I think it's search is how you pronounce
it.
The CRX, I think it's CRXNG now.
Searching, I think is how it's pronounced.
I used to use the crx.be instance,
which I think is still around.
And I will admit the results were
impressive.
I could always find the weirdest niche
stuff that I couldn't find anywhere else.
Because it drew from so many different
search engines.
But yeah, at the end of the day,
personally,
I decided that what I really wanted was
like an independent index that wasn't just
a meta search engine.
So that's one of the reasons that I
went with Brave.
But yeah, I'm with you.
They're all different.
I think it's totally valid to just try
out different ones and see which one works
best.
That's kind of really it for questions,
I think.
We did have another comment here.
Somebody said, happy birthday, privacy.
Is that in reference to Data Privacy Day
recently?
Or is this when Privacy Guides was
founded?
I'm not sure.
I feel like I should know that.
Yeah, I don't know.
It seems an interesting comment to make.
Thanks, I think.
You know,
I will take this as an excuse to
go get some cake after this.
I'm down.
We'll put it on the company card.
I don't have a company card.
Jonah, I want a company card.
I'm kidding.
I just like saying random stuff.
And then, yeah,
one last person left a comment when we
were talking about AI.
They said use local AI instead.
Yeah,
I think local AI is probably going to
be best for, again, end user privacy,
especially because a lot of them you can
completely firewall them on your computer
or your device and they never have to
touch the internet.
But again, we were also talking,
I know I'm like really beating it over
the head lately,
but just the idea of like,
it's still trained on user data that may
not have been consensually collected in a
lot of cases.
There's several ongoing lawsuits about
this very issue right now of copyrighted
works that, and actually,
you mentioned it earlier and I completely
forgot to bring it up,
but I think that's so funny that Sam
Altman is like, oh, well,
if we can't steal copyrighted material,
then we don't have a business.
And it's like, okay,
Like,
could you imagine a drug dealer using that
in court?
Like, well, your honor,
if I can't cook meth,
then I don't have a business.
And it's like, well, meth is illegal.
So that sounds like a you problem.
Like,
that's insane that they're even trying to
use that as a defense.
And it's like, well,
if I can't steal everybody's property,
then I don't have a business.
It's like, then you don't have a business.
That's how it works.
Sorry.
I know I'm ranting a little bit,
but the nerve to use that.
All right.
I think that's all we got this week.
So let me...
pull up my notes here.
All right,
so all the updates from this week in
privacy are already shared on the blog,
actually.
We have actually,
in case you guys didn't know,
we now are sending the blog post out
at the same time that we start streaming.
So if you want,
you can go sign up for the newsletter
and subscribe on your favorite RSS reader
and you will get a reminder.
There's a link to the StreamYard stream
right there in the newsletter,
so it's a really easy way to get
a reminder and start watching.
For people who prefer audio,
we offer an audio podcast available on all
podcast platforms and RSS,
and the video will also be synced to
PeerTube.
These will be after the fact.
Privacy Guides is an impartial nonprofit
organization that is focused on building a
strong privacy advocacy community and
delivering the best digital privacy and
consumer technology rights advice on the
internet.
If you want to support our mission,
you can make a donation on our website,
privacyguides.org.
To make a donation,
click the red heart icon located in the
top right corner of the page.
You can contribute using standard fiat
currency via debit or credit card,
or opt to donate anonymously using Monero
or your favorite cryptocurrency.
Becoming a paid member unlocks exclusive
perks like early access to video content
and priority during the This Week in
Privacy livestream Q&A.
You'll also get a cool badge on your
profile in the forum and the warm fuzzy
feeling of supporting independent media.
Thank you guys so much for tuning in
this week,
and we will be back next week with
more news.
Bye, everybody.